俄罗斯黑客组织APT44(Sandworm)使用“Army+”主题开展对乌克兰网络攻击
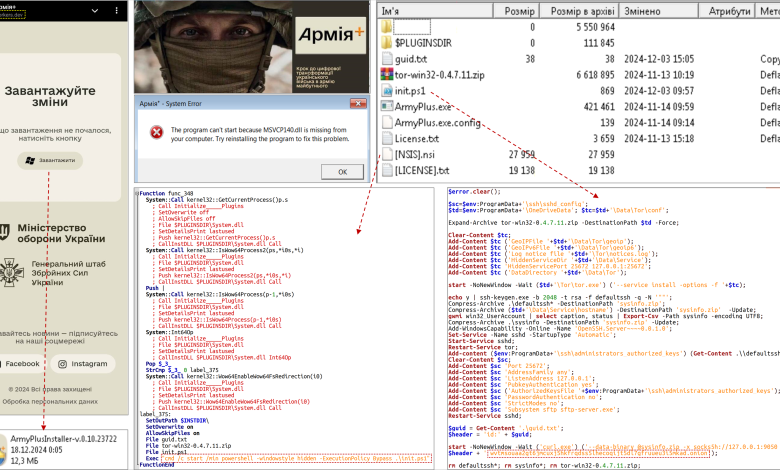
2024年12月17日,乌克兰CERT-UA政府计算机应急响应小组收到MIL.CERT-UA专家的信息,称检测到一些模仿“Army+”应用程序官方页面并使用Cloudlfare Workers发布的网络资源服务。
如果访问上述网站,用户可以下载可执行文件“ArmyPlusInstaller-v.0.10.23722.exe”(名称更改)。
该 EXE 文件被发现是使用 NSIS(Nullsoft 脚本安装系统)创建的安装程序,其中除了 .NET 诱饵文件“ArmyPlus.exe”外,还包含 Python 解释器文件、Tor 程序文件的存档和 PowerShell脚本“init.ps1”。
如果打开“ArmyPlusInstaller-v.0.10.23722.exe”文件,将会启动一个诱饵文件以及一个PowerShell脚本,其目的是:
- 在受害者的计算机上安装 OpenSSH 服务器
- RSA 密钥对生成
- 将公钥添加到“authorized_keys”文件中进行身份验证
- 使用“curl”将私钥发送到攻击者的服务器(TOR 地址)
- 使用 Tor 发布隐藏的 SSH 服务。
这样,就为远程秘密访问受害者的计算机创造了技术可能性。
上述活动由 CERT-UA 在 UAC-0125 标识符下进行跟踪,并且具有足够的置信度,与 UAC-0002 集群(APT44 又名 Sandworm)相关联。同时,在2024年上半年发生的事件中,主要的感染媒介是Microsoft Office程序包(例如“Office16.iso”,MD5:79782773ffee7b8141674c27e9bfc109),其中包含木马组件“omas” -x-none.msp”(MD5: 08a0c1166d8e50d95254b198b8168726),其中包含带有 PowerShell 命令的文件“CommunicatorContentBinApp.cmd”(MD5:4316eb790d186ffda2999257f8ded747)。
我们强调,在成功渗透并对影响对象产生兴趣的情况下,攻击者将进一步对组织的信息和通信系统发起网络攻击。
文件:
0799756f104a70cb6ce0cfc422de25db d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2 ArmyPlusInstaller-v.0.10.23672.exe a27a90a685dad9fc7f1c5962f278f197 4dca04f1e16cbe88776a3187031cff64981155cb3b992031250c6fed40496318 ArmyPlusInstaller-v.0.10.23722.exe 52853b39922251a4166a5b032e577e7a 86039bc8b1a6bb823f5cbf27d1a4a3b319b83d242f09ffcd96f38bbdbbaaa78f init.ps1 ed0c7c1925ac23bd8b4d09e77aabb0ee 8ba4c3ede1ed05a3ad7075fee503215648ec078a13523492e2e91a59fa40c8da guid.txt a2f355057ade20d32afc5c4192ce3986 b663e08cc267cdb7a02d5131cb04b8b05cb6ad13ac1d571c6aafe69e06bf8f80 ArmyPlus.exe (приманка)
网络:
(для workers[.]dev піддомени не наводяться) desktopapluscom.workers[.]dev desktopaplus.workers[.]dev armyplus-desktop.workers[.]dev aplusdesktop.workers[.]dev armylpus.workers[.]dev aplusmodgovua.workers[.]dev wvtmsouaa2gt6jmcuxj5hkfrqdss5lhecoqijt5dl7gfruueu3i5mkad[.]onion
图片信息